ROB ENGELAAR/AFP/Getty Images
A new WikiLeaks Vault 7 leak titled “ESLA” claims that the Central Intelligence Agency can track the location of laptops by intercepting the surrounding WiFi signals. The 42-page report can be read here.
A summary of the new report by WikiLeaks reads:
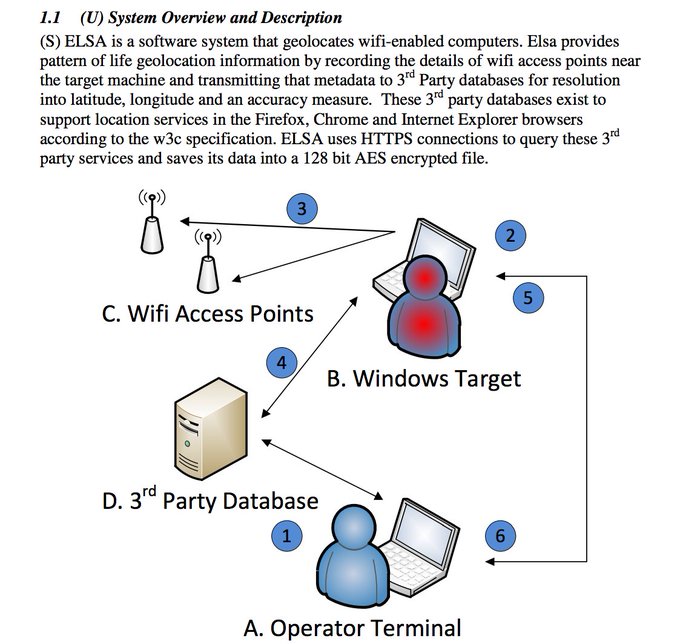
Today, June 28th 2017, WikiLeaks publishes documents from the ELSA project of the CIA. ELSA is a geo-location malware for WiFi-enabled devices like laptops running the Micorosoft Windows operating system. Once persistently installed on a target machine using separate CIA exploits, the malware scans visible WiFi access points and records the ESS identifier, MAC address and signal strength at regular intervals. To perform the data collection the target machine does not have to be online or connected to an access point; it only needs to be running with an enabled WiFi device. If it is connected to the internet, the malware automatically tries to use public geo-location databases from Google or Microsoft to resolve the position of the device and stores the longitude and latitude data along with the timestamp. The collected access point/geo-location information is stored in encrypted form on the device for later exfiltration. The malware itself does not beacon this data to a CIA back-end; instead the operator must actively retrieve the log file from the device – again using separate CIA exploits and backdoors.
The ELSA project allows the customization of the implant to match the target environment and operational objectives like sampling interval, maximum size of the logfile and invocation/persistence method. Additional back-end software (again using public geo-location databases from Google and Microsoft) converts unprocessed access point information from exfiltrated logfiles to geo-location data to create a tracking profile of the target device.
This is the latest release of WikiLeaks since last week when “Brutal Kangaroo” was announced. Brutal Kangaroo “is a tool suite for Microsoft Windows that targets closed networks by air gap jumping using thumbdrives.”
While many of the WikiLeaks have to do with Windows OS, earlier this year it was leaked by WikiLeaks that the CIA allegedly bugs “factory fresh” iPhones.