A massive ransomware attack has that began last week has infected computers around the world, locking up computers at hospital, major companies and government offices, CNN reports.
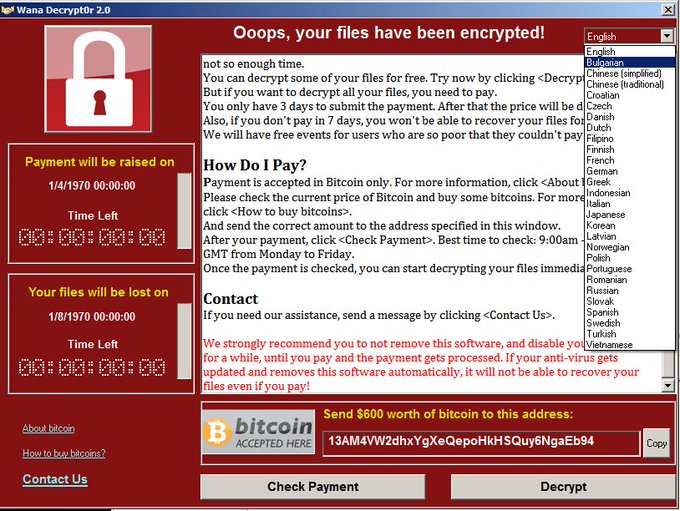
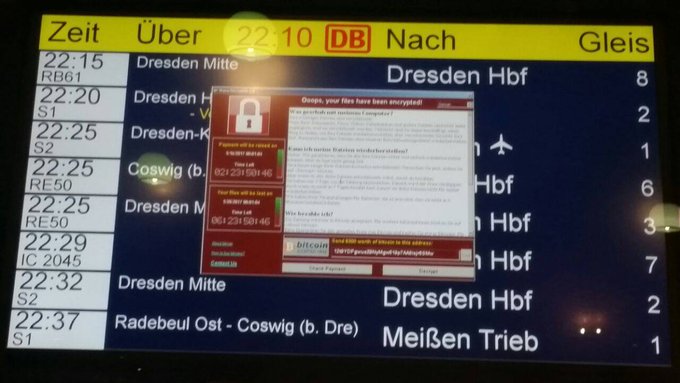
The cyber-attack takes over computer systems, shutting them down and demanding a ransom payment of $300 in bitcoin to have the computer unlocked, according to CNN. The infected computers are frozen with a red message stating “Oops, your files have been encrypted!” appearing on the locked screen along with the ransom demand. There have been more than 200,000 machines hit by the attack since it began last Friday, CNN reports.
Victims of the attack include FedEx, Nissan, Deutsche Bahn railway, Hitachi, the Russian Central Bank, Telefonica and the British National Health Service. The culprits are not yet known, the Associated Press reports.
“We don’t expect this to be a sophisticated group,” Tim Wellsmore, of the the California-based network security company FireEye, told the Associated Press. “We expect this is a small operation that is undertaking this. They just happen to hit the motherlode. Unfortunately for the rest of us, this thing went quite global quite quickly.”
The hackers were using tools stolen from the U.S. National Security Agency and released on the Internet, the Associated Press reports. The software vulnerability was first identified by the NSA for its own intelligence-gathering work, according to the AP.
Here’s what you need to know:
1. Experts Are Calling It the Largest Cyber-Attack in History
Experts are calling the WannaCry ransomware incident the largest cyber-attack in history, CNN reports. Microsoft, the operating system targeted, has called it a “wake-up call” for governments.
But the attacks occur everyday, experts told the Associated Press.
“It’s a business model that works and you don’t need a lot of investment to actually get a decent return,” Tim Wellsmore, of FireEye, a network security company, told the AP. “You can buy ransomware kits on the dark web, you can buy all the tool sets you need to undertake your own ransomware campaign quiet easily,” he said, referring to an area of the internet often used for illegal activity. Would-be extortionists can launch a global campaign with little effort, yet authorities can do little because it’s very difficult to investigate.”
2. The Ransomware Infected Computers in at Least 150 Countries & the Attackers Have Collected About $50,000 From the Victims So Far
The ransomware attack had infected computers in at least 150 countries by Monday, CNN reports. Bitdefender told CNN about $50,000 has been collected by the attackers since Friday.
The threat has started to subside, but experts warn it is still out there.
“We will get a decryption tool eventually, but for the moment, it’s still a live threat and we’re still in disaster recovery mode,” Europol director Rob Wainwright told CNN.
Israel Levy of the cybersecurity firm Bufferzone told CNN that once a computer in a network is infected, it spreads to all computers “within seconds.” Levy said if an office worker opens an infected PDF attached to an email, everyone in the office could be under attack. The ransomware came through phishing emails. Levy said it was “unheard of six months ago” that multiple machines could be targeted at the same time.
3. Microsoft Blasted the NSA for ‘Stockpiling’ Vulnerabilities & Says It’s Like the Military Having ‘Some of Its Tomahawk Missiles Stolen’

A computer running a Windows Server is seen connected into a network server in an office building in Washington, DC on May 13, 2017. (Getty)
Microsoft President and Chief Legal Officer Brad Smith blasted the National Security Agency for “stockpiling” vulnerabilities and allowing the hackers to gain access to it in a blog post on Microsoft’s website:
This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem. This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage. An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen. And this most recent attack
The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world. We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits. This is one reason we called in February for a new “Digital Geneva Convention” to govern these issues, including a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them. And it’s why we’ve pledged our support for defending every customer everywhere in the face of cyberattacks, regardless of their nationality. This weekend, whether it’s in London, New York, Moscow, Delhi, Sao Paulo, or Beijing, we’re putting this principle into action and working with customers around the world.
The NSA has not commented about WannaCry.
Security expert Rob Graham told Forbes “a lot of blame for having weaponized the exploit, then allowing it to leak to the internet.” Graham told Forbes it is “stupid” to believe the NSA would “unilaterally disarm itself” and “arms control trying to regulate such things is even stupider. “There’s no difference between legitimate software we use to test networks and evil software we use to hack into networks. Code is speech — there is no way of ‘controlling’ software that doesn’t also control speech/.”
4. A Killswitch Was Discovered, Limiting the Initial Impact of the Attack, but the Ransomware Has Been Updated Without It

A computer technician connects a computer into a network server in an office building in Washington, DC on May 13, 2017. (Getty)
A killswitch was discovered, which experts have credited with limiting the impact of the attack, according to CNet. A cyber security researcher found the kill switch accidentally. He was able to purchase an unregistered domain name for $10.69 to halt the attack, CNet reports. But the ransomware has since been updated.
“Hackers have since updated the ransomware, this time without the kill switch. New variations of the ransomware have popped up without the Achilles heel and bearing the name Uiwix, according to researchers at Heimdal Security,” Alfred Ng wrote on the website.
The cyber security researcher has been identified as Marcus Hutchins, a 22-year-old English computer programmer who went by the name Malware Tech. He wrote about his actions in a blog post on his website titled “How to Accidentally Stop a Global Cyber Attack”:
I was quickly able to get a sample of the malware with the help of Kafeine, a good friend and fellow researcher. Upon running the sample in my analysis environment I instantly noticed it queried an unregistered domain, which I promptly registered.
We prevented the spread of the ransomware and prevented it ransoming any new computer since the registration of the domain (I initially kept quite about this while I reverse engineered the code myself to triple check this was the case, by by know Darien’s tweet had gotten a lot of traction.
Hutchins warned that another attack could be coming on May 15.
“It’s very important that people patch their systems now. We have stopped this one, but there will be another one coming and it will not be stoppable by us,” Hutchins told the BBC. There’s a lot of money in this. There’s no reason for them to stop. It’s not really much effort for them to change the code and then start over. So there’s a good chance they are going to do it… maybe not this weekend, but quite likely on Monday morning.”
5. Microsoft Has Released Updates to Its Older, Unsupported Operating Systems, Like XP & Windows 2003, Which Were the Most Vulnerable

A message informing visitors of a cyber attack is displayed on the NHS website on May 12, 2017 in London, England. (Getty)
Microsoft that it had already released a security update to patch the vulnerability exploited by the ransomware, but thousands of computers remained vulnerable to the WannaCry attack two months after the update was released, NPR reports.
According to NPR, the most vulnerable computers were using older operating systems, like Microsoft XP and Windows 2003. The software giant made the rare move of providing updates to those unsupported operating systems on Friday, NPR reports. Other computers were vulnerable because users had not updated their systems with the security patch. Microsoft and experts say computer users can avoid becoming victims of this attack and similar ones by updating their machines when security patches are released. Brad Smith, the president and chief legal office of Microsoft, said in a post on the company’s website that the customers must take precautions:
This attack demonstrates the degree to which cybersecurity has become a shared responsibility between tech companies and customers. The fact that so many computers remained vulnerable two months after the release of a patch illustrates this aspect. As cybercriminals become more sophisticated, there is simply no way for customers to protect themselves against threats unless they update their systems. Otherwise they’re literally fighting the problems of the present with tools from the past. This attack is a powerful reminder that information technology basics like keeping computers current and patched are a high responsibility for everyone, and it’s something every top executive should support.
At the same time, we have a clear understanding of the complexity and diversity of today’s IT infrastructure, and how updates can be a formidable practical challenge for many customers. Today, we use robust testing and analytics to enable rapid updates into IT infrastructure, and we are dedicated to developing further steps to help ensure security updates are applied immediately to all IT environments.
Smith said in his post, “We need the tech sector, customers, and governments to work together to protect against cybersecurity attacks. More action is needed, and it’s needed now. In this sense, the WannaCrypt attack is a wake-up call for all of us. We recognize our responsibility to help answer this call, and Microsoft is committed to doing its part.”