
The biggest Apple account theft has occurred according to a security firm from Palo Alto. 225,000 unlocked or jailbroken phones were hacked and information was stolen by a company in China. Users with normal iPhones don’t need to worry but if you have an unlocked or jailbroken phone you may need to watch what you download.
Here’s what you need to know:
1. The Attacks Only Affect Unlocked and Jailbroken Phones

Jailbraking an iPhone involves removing hardware restrictions so the user can access apps and extensions that you can’t access through the App Store. That is where the hackers found their in.
2. At Least 225,000 Users Were Affected
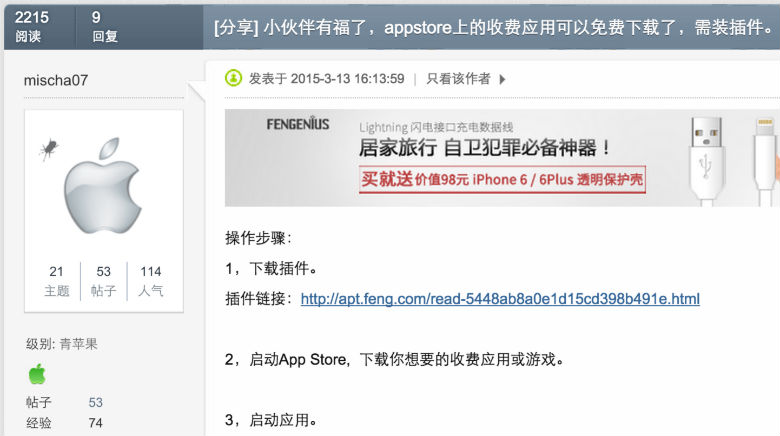
The Chinese software company tricked users into downloading the malware through apps and software meant for unlocked phones.
3. The Malware, Called KeyRaider, Steals Apple Account Information

KeyRaider intercepts all iTunes traffic done on the device. If you have it downloaded to your phone, every time the user logs the app store, usernames, passwords, private keys and purchasing receipts are sent directly to the hackers.
4. This is The Largest Apple Account Breach

According to Palo Alto Networks, a security company, this is the largest breach Apple has seen. The attack hit 18 countries including the US.
5. The Hackers Are Giving Away The Software

Even if the hackers are caught, it won’t be the end of the information theft. The company is giving away copies of the software for free and 20,000 people have already downloaded it. If you believe you may have downloaded the suspicious software, Palo Alto Networks laid out a list of what to do next. We recommend staying away from an unlocked phone altogether.