As privacy awareness grows, the dark web has presented a more appealing and secure browsing alternative for some users compared to popular browsers.
The dark web is a network of websites that only run on anonymous browsers, which will hide the identity of the user and the people who run the sites. Perhaps the best-known anonymous browser is Tor, a platform that supports about 60,000 services like websites and chat services. It is legal to use Tor, but it does host illegal content.
In the popular imagination, anonymous browsers are a breeding ground for criminals. While the dark web does provide cover for illegal activities like storing child pornography or buying banned drugs, it also asserts a need for privacy that is often ignored on the larger Web.
Here’s what you need to know about Tor:
1. It Protects the Identity of the User Through ‘Hopping’ Across Devices Worldwide

There are about 350,000 daily users of Tor in the US (Wikimedia)
In order to protect your identity, Tor sends your communication through a random path in a network of relays until it reaches its destination. Tor will bounce your internet request across the network. This circuitous path will make it seem as if the request was coming from another device. While this process can make searching Tor agonizingly slow, it is the framework for anonymous browsing.
There are some limitations to anonymous browsing. While traffic within the Tor network is encrypted, it becomes visible when it retrieves information from the destination. Researchers have shown it’s possible to eavesdrop on traffic from these exit nodes. This is why it is important to use encrypted connections like HTTPS, identified by the green lock and https:// in the address bar. Here are some other activities that may compromise your identity on Tor:
- Torrenting
- Using a Browser Plugin
- Downloading and opening a document while online
- Filling out web forms with personal information
Tor will encrypt your data within its network. Each computer node your message passes through will decrypt your data one layer at a time (hence the name ‘onion router’) to find out where to send the message to next. Limiting access to information every step in the process has foiled most snooping attempts.
2. To Find a Site on Tor You Need to Know the Address of the Onion Service
The home page for the Tor browser (Wikimedia)
Sites only available on the Tor network are known as Onion services. To help keep the services anonymous, the sites are only accessible through sixteen mostly random letters and numbers followed by “.onion”, according to the Tor Browser User Manual. The list of Onion Services include marketplaces dedicated to making cryptocurrencies like Bitcoin untraceable and selling drugs.
3. Less Than Half of the Activity on the Dark Web is Illegal

The dark web is not as dark as it appears (Getty)
Despite its nefarious undertones, much of the activity on the dark web is legal and even trivial. About 55 percent of content on the dark web is legal, according to Terbium Labs, a dark web data intelligence provider. Terbium Labs crawled 400 random sites one day in August for the study. So what kind of legal content lives on the dark web? Tor users can access websites like the dark-web replicas of popular sites like Facebook and ProPublica.
While some users seek the dark web as a sanctuary for illegal activities, others use it to safeguard their right to privacy. In fact, the public appetite for decentralized exchanges extends to cryptocurrencies like Bitcoin, as more people seek relief from the vice grip of surveillance nets. Here are some legitimate reasons people use Tor, according to the Tor Project.
- Journalists who need to communicate with whistleblowers safely
- NGO workers abroad who use Tor to connect to their home websites
- The US Navy’s intelligence gathering missions
- Rape and abuse survivors who seek anonymous forums
4. The Dark Web Was Originally Meant to Safeguard Government Communications
“Onion Routing” was originally developed in order to protect intelligence communications online. The United States Naval Research Laboratory created Tor in the mid-1990s. The project was transferred to the Defense Advanced Research Projects Agency (DARPA) in 1997 and underwent its first round of software testing on 20 September 2002. Tor was publicly launched a year later.
Since the Naval Research Laboratory released Tor’s code under a free license in 2004, privacy advocates have championed the software. The digital rights group Electronic Frontier Foundation funded Tor’s continued development. Tor’s developers founded the nonprofit The Tor Project to maintain Tor.
5. Anyone Can Volunteer to Be Part of Network Running Tor
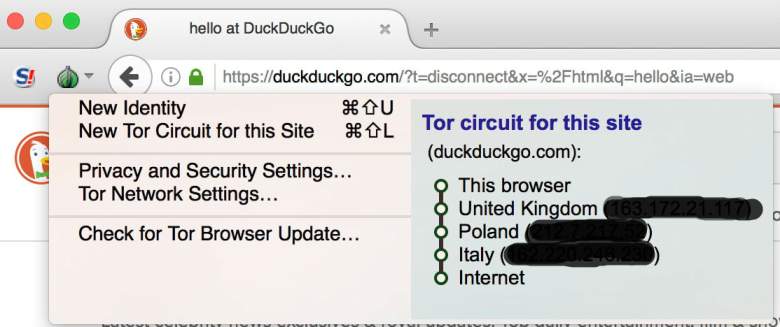
You can sign up as a relay on Tor
Anyone can volunteer their computer to be part of the Dark Web network. As the number of volunteer relays grow, so does the network’s speed. Tor relays can run on almost all operating systems, but works best for current distributions of Linux, according to the Tor Project. You can also contribute to the Tor community simply by downloading and using the service. As more people use the Dark Web, the level of anonymity increases, because it becomes harder to single out users.