Symantec/Twitter The "Petya" ransomware attack has hit companies in and government agencies in Europe and the United States.
Another massive cyberattack has struck several companies and government agencies in Europe and the United States, The Guardian reports.
Symantec, a cyber security firm, told the newspaper that the “Petya” ransomware being used in the attack is using the same exploit to take advantage of software vulnerability as the WannaCry ransomware that hit thousands of computers around the world last month.
The attack began Tuesday morning with computers in Ukraine before spreading across Europe and eventually to the United States, according to The Telegraph.
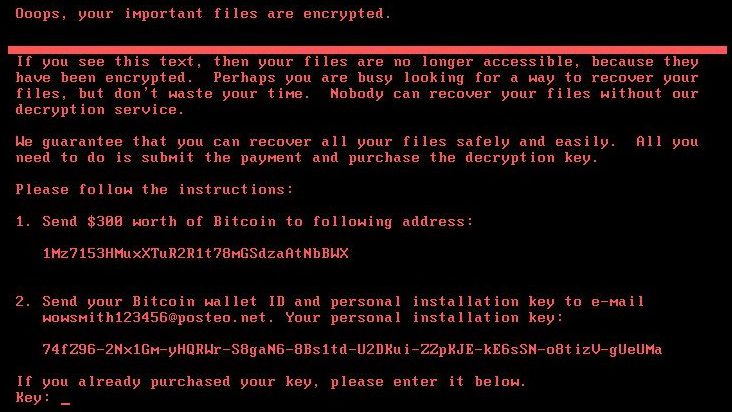
According to Symantec, a ransom note is “displayed on infected machines, demanding that $300 in bitcoins be paid to recover files.”
Symantec says, “Petya propagates itself by exploiting the MS17-010 vulnerability, also known as Eternal Blue,” in Microsoft. “Symantec continues to investigate other possible methods of propagation.”
Here’s what you need to know:
1. The Kaspersky Lab Says the Attackers Are Actually Using a New Form of Ransomware It’s Calling ‘NotPetya’ & About 2,000 Computers Have Been Hit
The “Petya” ransomware was first spotted in 2016, according to Symantec.
“Petya has been in existence since 2016. It differs from typical ransomware as it doesn’t just encrypt files, it also overwrites and encrypts the master boot record (MBR),” Symantec says.
But while Symantec and others are reporting the ransomware to be Petya or a version of Petya, the Kaspersky Lab, another cyber security firm, says it is actually a new form of ransomware not seen before, which it is calling “NotPetya.”
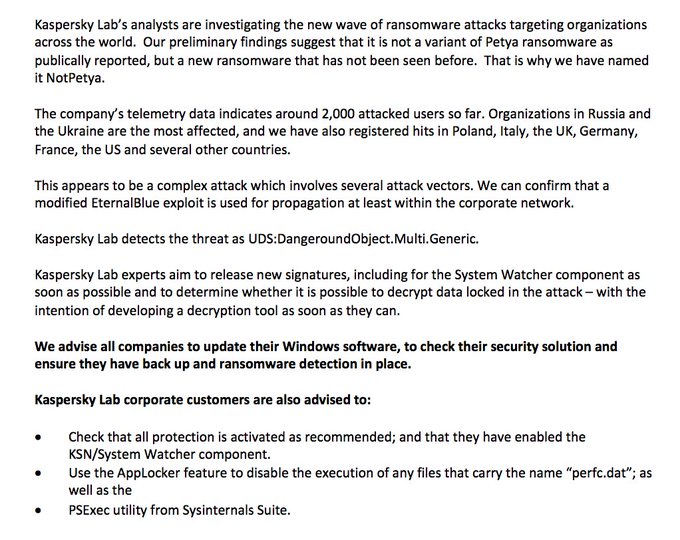
“Kaspersky Lab’s analysts are investigating the new wave of ransomware attacks targeting organizations across the world. Our preliminary findings suggest that it is not a variant of Petya ransomware as publically reported, but a new ransomware that has not been seen before. That is why we have named it NotPetya,” Kaspersky Lab said on Twitter.
According to Kaspersky, about 2,000 computers have been attacked so far.
“Organizations in Russia and Ukraine are the most affected, and we have also registered hits in Poland, Italy, the UK, Germany, France, the US and several other countries,” Kaspersky Lab says. “This appears to be a complex attack which involves several attack vectors. We can confirm that a modified EternalBlue exploit is used for propagation at least within the corporate network.”
According to Kaspersky, companies should update their Windows software, “check their security solution and ensure they have back up and ransomware detection in place.”
Symantec reports that at least nine BitCoin payments have been made to the attackers. Government agencies and experts warn not to pay.
“Just like WannaCry, organizations are locked out of their networks and a fee demanded to decrypt files,” Travis Farral, the director of security strategy at the tech firm Anomali, told The Sun. “Bitcoin payments are currently already at $2,000+ already. But it’s essential that victims understand that payment may not actually allow them to access their data, and may just fund hackers to commit further crimes.”
2. The Attack First Struck Government & Business Computers in Ukraine Before Spreading to Major European Firms Like Maersk
The attacks first struck computers in the Ukraine, crippling government offices, the central bank, a state-run aircraft manufacturer, airports, public transportation and several firms, according to The Telegraph.
It then began spreading across Europe, The Telegraph reports. Major businesses, like the Dutch-based shipping firm Maersk, were among the additional victims.
“We got the news that Ukraine was under attack and we received some reports from customers that they were being infected with ransomware,” McAfee scientist and principal engineer Christiaan Beek told Wired. “It’s massive. Complete energy companies, the power grid, bus stations, gas stations, the airport and banks are being targeted.”
He told Wired he believes the attack was designed for “speed and spreading around like crazy.”
3. Pharmaceutical Company Merck & a Major Law Firm, DLA Piper, Are Among the Victims in the U.S.
Some companies in the United States have also been affected by the attack. The pharmaceutical firm Merck was among the first major victims, ABC News reports.
Merck, based in New Jersey, said on Twitter, “We confirm our company’s computer network was compromised today as part of global hack. Other organizations have also been affected. We are investigating the matter and will provide additional information as we learn more.”
The Washington D.C. office of the law firm DLA Piper was also hit, according to Politico.
“All network services are down, do not turn on your computers! Please remove all laptops from docking stations and keep turned off. No exceptions,” a message posted at the office said Tuesday, according to Politico. A client told Politico that DLA Piper’s secure document system for clients was down, possibly as a precaution.
“A bit stressed at moment as I am unsure if our docs there are safe,” the client told the news site.
A Pennsylvania hospital system was also hit by a cyber attack on Tuesday, WTAE-TV reports, but it is not clear if it is connected to the other attacks.
A spokesperson for the Heritage Valley Health System, Suzanne Saskon, told the news station computers throughout the entire system, which includes two hospitals along with several doctors’ offices and other facilities in Allegheny, Beaver and Lawrence counties.
“Heritage Valley Health System has been affected by a cybersecurity incident. The incident is widespread and is affecting the entire health system including satellite and community locations,” Sakson said in a statement. “We have implemented down time procedures and made operational adjustments to ensure safe patient care continues unimpeded.”
4. The U.S. Department of Homeland Security & Europol Are Both Monitoring & Investigating the Attack
The U.S. Department of Homeland Security and Europol both issued statements Tuesday saying they are monitoring and investigating the attacks.
“The Department of Homeland Security is monitoring reports of cyber attacks affecting multiple global entities and is coordinating with our international and domestic cyber partners. We stand ready to support any requests for assistance,” the U.S. agency said. “Upon request, DHS routinely provides technical analysis and support. Information shared with DHS as part of these efforts, including whether a request has been made, is confidential.”
Europol said in a statement on Twitter, “We are aware of a (developing) ransomware attack & are liaising w/ cyberunits in EU & key industry partners to establish full nature of this attack.”
5. The ‘WannaCry’ Attack Hit More Than 230,000 Computers Last Month
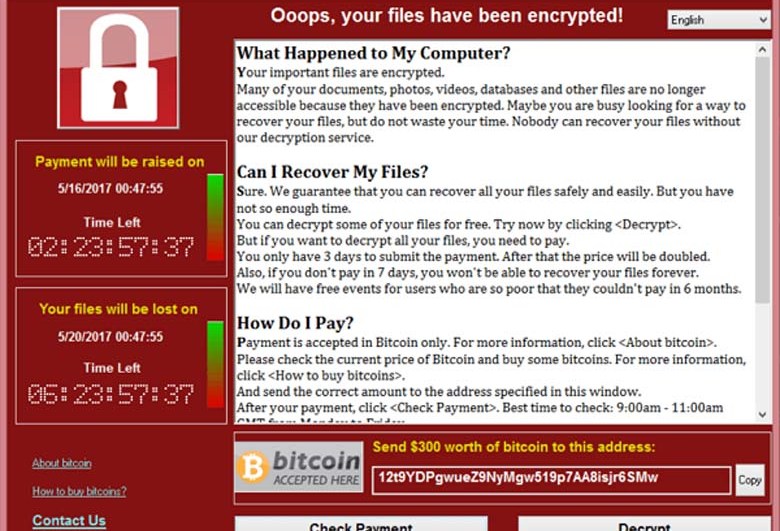
The WannaCry warning.
The latest cyber-attack comes just weeks after hackers used another ransomware virus, WannaCry, to strike more than 230,000 computers around the world.
WannaCry first hit computers on May 12 and then continued until Monday, May 15, when a vulnerability in older Microsoft operating systems was patched, according to NBC News.
The cyber-attack took over computer systems, shutting them down and demanding a ransom payment of $300 in bitcoin to have the computer unlocked, according to CNN. The infected computers are frozen with a red message stating “Oops, your files have been encrypted!” appearing on the locked screen along with the ransom demand.
An “accidental hero,” Marcus Hutchins, also stopped the spread of the attack by registering a website that became a “kill-switch” for the ransomware, The Guardian reported.
The hackers were using tools stolen from the U.S. National Security Agency and released on the Internet, the Associated Press reported. The software vulnerability was first identified by the NSA for its own intelligence-gathering work, according to the AP.