
(Ashley Madison / Pirate Bay)
Where can you find a copy of the list of the 32 million Ashley Madison cheaters, released by the Impact Team hackers? First you’re going to need a bittorrent client, such as “Transmission.” It’s free and easy to use and can be downloaded here.
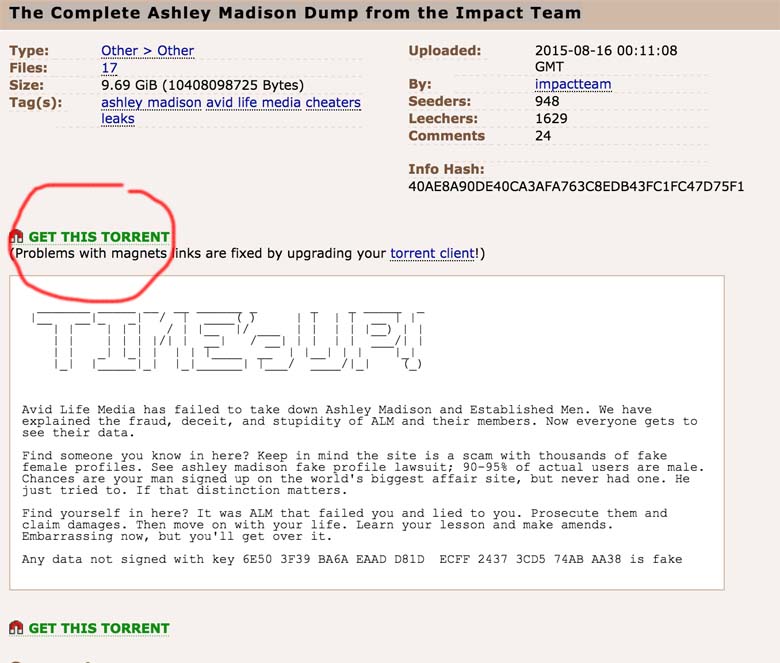
Once you have Transmission installed, go to a peer-to-peer file sharing like The Pirate Bay. To be taken to The Pirate Bay, click here. Once there, search “Ashley Madison”, or click here for a direct link to the verified torrent file titled “The Complete Ashley Madison Dump from the Impact Team.”
Then click on the “Get This Torrent” as shown below in red.
(The Pirate Bay)
Follow your computer’s promps and open the torrent in Transmission. Due to the demand of the list, current wait time for downloading it can take anywhere from two hours to two days right now. Leave the program running while it’s downloading, and once it’s done being downloaded, close out.
If you decide to not use Pirate Bay or its URL is inaccessible in your country, use another torrent site but the “magnet number” for the torrent should read “40ae8a90de40ca3afa763c8edb43fc1fc47d75f1.” A magnet number is like an ISBN or catalog number for a torrent and is usually posted somewhere in its content information.
You now have the Complete Ashley Madison Dump from the Impact Team, which according to Wired.com:
The files appear to include account details and log-ins for some 32 million users of the social networking site, touted as the premier site for married individuals seeking partners for affairs. Seven years worth of credit card and other payment transaction details are also part of the dump, going back to 2007.
Of the 32 million emails in the list, The Hill reports 15,000 of them are government-related email addresses.
Read more about Ashley Madison in Spanish at AhoraMismo.com:

