Getty
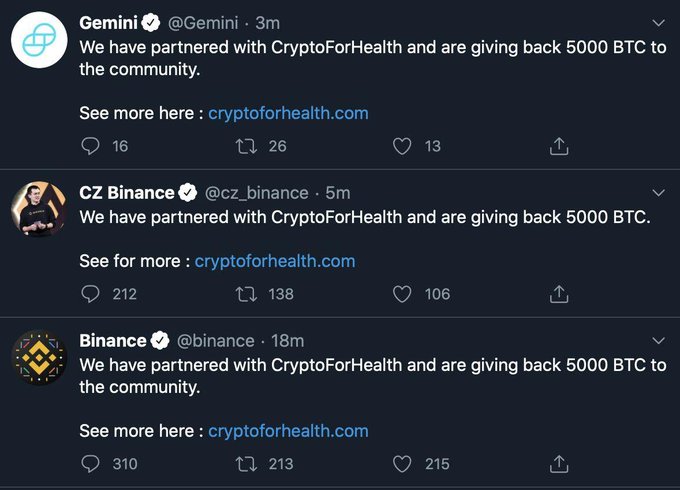
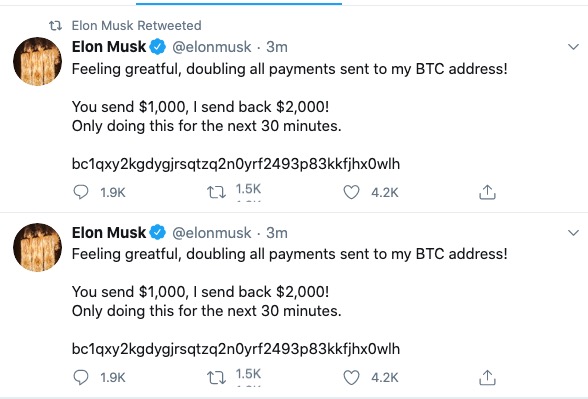
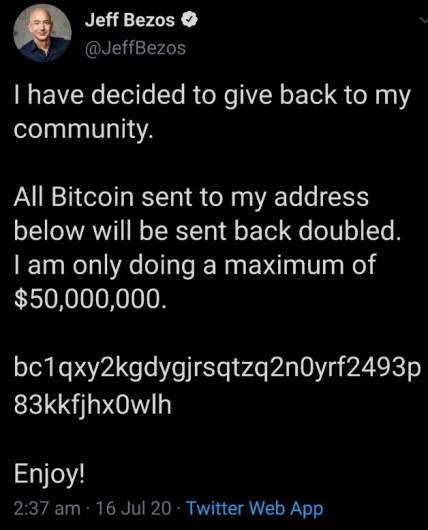
A website called CryptoForHealth is apparently tied to the Twitter hack that scammed for than $100,000 in Bitcoin from unsuspecting people. The hack took over a number of Twitter accounts, including Apple, Elon Musk, Jeff Bezos, Mike Bloomberg, and more. Some of the early versions of the hack were focused on cryptocurrency Twitter accounts sharing a CryptoforHealth website.
Early tweets associated with the hack pointed people to the CryptoforHealth website.
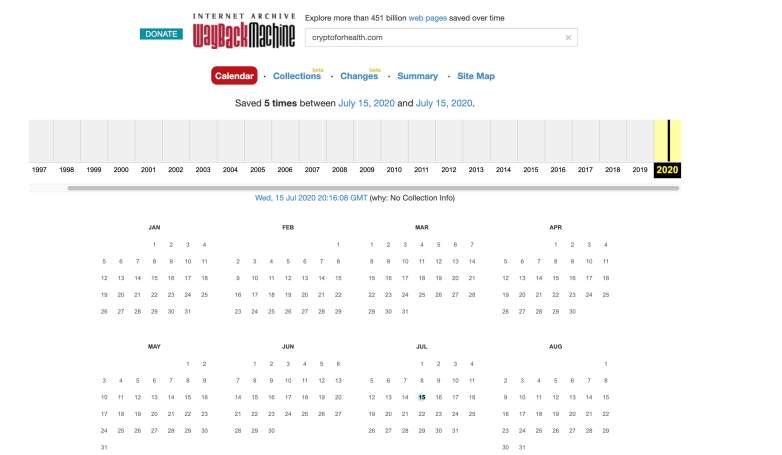
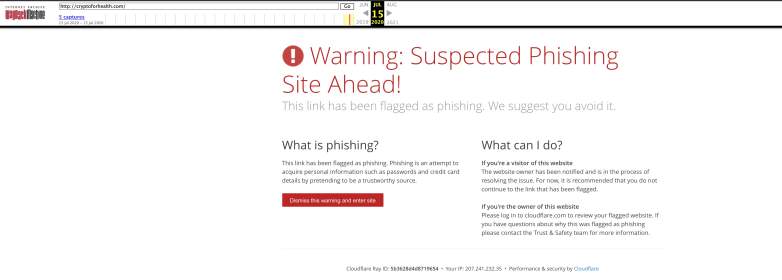
A look at Internet archives for CryptoforHealth.com revealed that the site did not appear until today and now it’s been flagged as a phishing site.
Here is what the website looked like before it was flagged, according to Internet Archive.
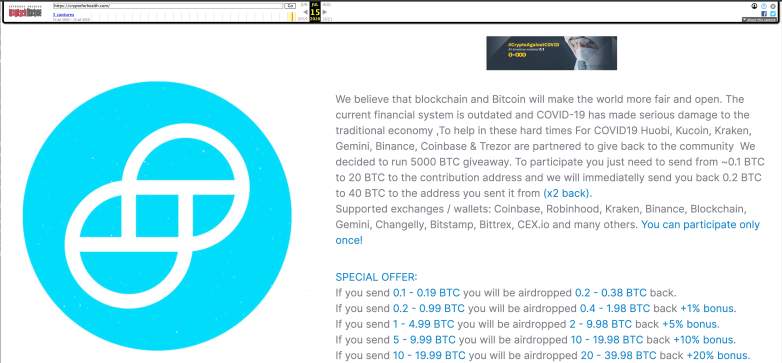
The webpage was titled “COVID 19 Giveaway” and then reads:
We believe that blockchain and Bitcoin will make the world more fair and open. THe current financial system is outdated and COVID-19 has made serious damage to the traditional economy , To help in these hard times For COVID19 Huobim, Kucoi, Kraken, Gemini, Binance, Coinbase & Trezor are partnered to give back to the community. We decided to run 5000 BTC giveaway. To participate you just need to send from 0.1 BTC to 20 BTC to the contribution address an we will immediately send you back 0.2 BTC to 40 BTC to the address you sent it from (x2 back.)
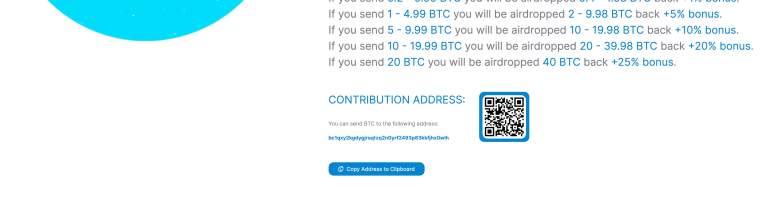
The site then offers a number of “special offers” for sending Bitcoin, including percent bonuses for specific amounts.
The site used the same Bitcoin contribution address that later appeared in scam tweets on hacked Twitter accounts like Elon Musk’s, Bill Gates’, Jeff Bezos’, and Apple’s.
Some Twitter accounts had even noted that they used strong passwords and 2 Factor Authentication, making it unclear how some of the accounts were hacked.
There’s now a phishing warning on the CryptoForHealth site.
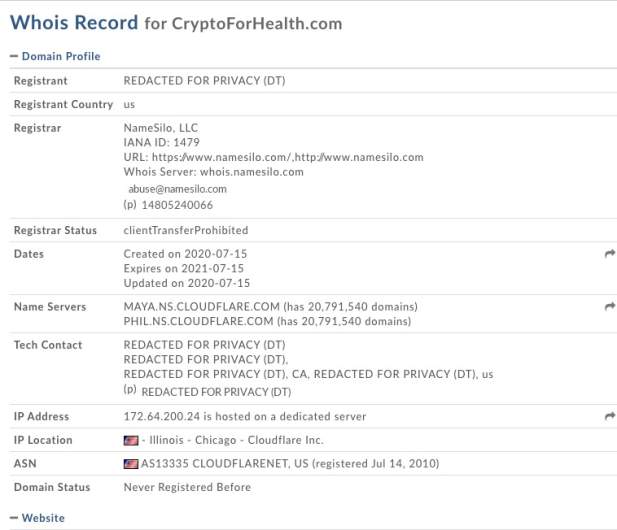
People who visited the WhoIs record for CryptoforHealth.com earlier on July 15 noted that some of the domain registration information wasn’t private at that time. However, it’s not clear if a sophisticated hack would use authentic information when registering the account. A name was listed on the WhoIs information, but it’s not clear if they were actually connected to the hack. The information on the WhoIS account listed a name from Vacaville, California.
The current WhoIs information is now private and labeled “redacted for privacy.”
According to ICANN, the domain was registered on July 15, 2020, the same day as the hack.
The Hacker Has Made More than $100K So Far
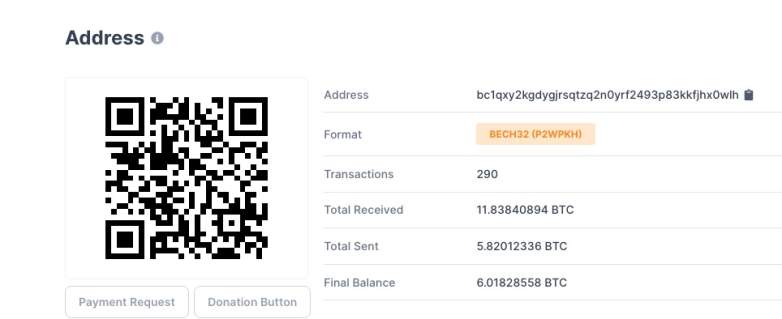
Using Bitcoin Explorer to track the Bitcoin address that was tweeted from Musk’s account, Heavy found that the address had 88 transactions with a total of 1.69691376 BTC received and 0.00000000 BTC sent as of 4:28 p.m. Eastern, just a few minutes after the first tweet. The number grew fast from there. As of 4:30 p.m., the transactions were at 111 with 2.48638415 BTC received and none yet sent. Then by 4:51 p.m. Eastern, there were 202 transactions and more than 5.85 BTC sent. Then later, as of 5:04 p.m., the account had received 6.45364473 BTC and had sent 1.04832256 BTC.
As of 5:30 p.m. Eastern, more than 290 transactions had appeared in the hacker’s Bitcoin address, according to Blockchain Explorer. This included more than 11.8 BTC received and more than 5.82 BTC sent.
With Bitcoin worth more than $9,200, that’s more than $108,000 sent to the hackers so far.